Overview
- Time: 1 hour (5 introduction, 25 teaching, 25 activity, 5 wrap-up)
- Objectives
- Understand the essential principles of data security
- Know how to employ data security in your role at a nonprofit organization
Introduction
- Write down your daily schedule and mark any points in the day where you interface with data. If you have any marked points, write down what you do to secure your data in that process (ex: storing in a safe database, removing names from sensitive data over email, etc).
- Discuss with a partner how this mental exercise emphasized data touchpoints and note any perceived gaps in your current data security practices before convening with the entire group.
Essential Data Security Principles
Many organizations in the nonprofit sector serve potentially vulnerable populations, such as youth or houseless individuals, and they often work with large amounts of data shared between many individuals within an organization. Because of this, nonprofit staff members have an important responsibility to keep that data safe and private, both for the communities they serve and their organization itself. This unit will go through basic practices of data security and share tips on how to keep your data safe when working in a nonprofit environment.
What is data security and why is it important to nonprofits?
Data security relates to any practices utilized to protect the digital information your organization interfaces with and collects on a daily basis. For nonprofit organizations, this can be information on the individuals you serve, the donors that fund your organization, the structural and legal background of your organization, and so on. Needless to say, nonprofit organizations are full of important data that needs to be protected, but what does this look like in practice?
Take this scenario as an example. Tom works for an organization that helps to improve the literacy of local public school students from kindergarten through eighth grade. His coworker Jen is working with a new group of students today and asked to see their records in order to best prepare. To be helpful, Tom sends Jen an email containing a screenshot of the personal information on each student from their database. Do you think this was the right thing to do? If you answered no, you’d be correct! Email is not always a secure form of communication within which to send sensitive data and since Tom and Jen work with youth, a breach of the information on their students could violate FERPA policies. Jen thanks Tom for the help, but reminds him to not share this information over email again and recommends sending a password-protected link to the cloud-stored database in the future.
This is just one example of how data security can come into play into the daily operations of a nonprofit organization. It also shows how despite our best intentions, sometimes we just don’t realize the importance of data security, which is why the next section below will go over some important data security tips and tricks that would be especially relevant to your work at a nonprofit organization.
Data Security Tips & Tricks
- Only store and maintain data that is important to your organization, and destroy any that is no longer needed.
- We all have massive numbers of files and folders from our work over the years that it is easy to forget about the information that is contained in all of them. In order to limit a security risk, it is important to only retain that which is absolutely fundamental to your current work with the nonprofit.
- Backup your data.
- Outside of simply collecting lots of data, it is important to make sure you retain copies of that data – again, only data that is necessary to the organization. Backing up your data ensures that if there is a loss of data on your local machine, you will still maintain access to them in the cloud.
- Never send sensitive information over email.
- This one may seem a bit rudimentary, but it is easy to forget the sensitive nature of the personal information you work with when you are interacting with it on a daily basis.
- Update your software.
- As frustrating as it can be to have to take a break from your work to let your software update, it is absolutely essential to keep your systems up-to-date to prevent any data breaches that could pose a risk to your greater organization.
- Implement two-factor authentication wherever possible.
- According to data from NTEN, less than 50% of nonprofits enable multi factor authentication despite coordinating massive amounts of data between donors, stakeholders, and served populations. Enabling multi-factor authentication adds another layer of security to data that makes it much more difficult for a hacker to gain access to sensitive information.
- Know the legal requirements of your data.
- Depending on the populations your organization serves, you might be legally obligated to protect sensitive information on those individuals. This can be HIPAA, FERPA, or any other legal framework, and it is essential to the success of your organization that you are well versed in the requirements those frameworks hold you to. And when in doubt, always act as if the data should be private and secure it from risk.
Activity
Using your nonprofit as a case study, we are going to map out all of the data that your organization handles and the stakeholders associated with each. Taking the diagram below as a reference, first write down all data in individual circles. Then draw lines to the stakeholders associated with each, each in its own squares. Then star any points of data that you are associated with and on the line between yourself and the data, write down how you handle that data. Finally, bubble in any specific data security measures your organization takes towards that data. If there are any spaces where you are not sure what your organization does with that data or how it secures it, mark it with a question mark and be sure to ask your team after the session.
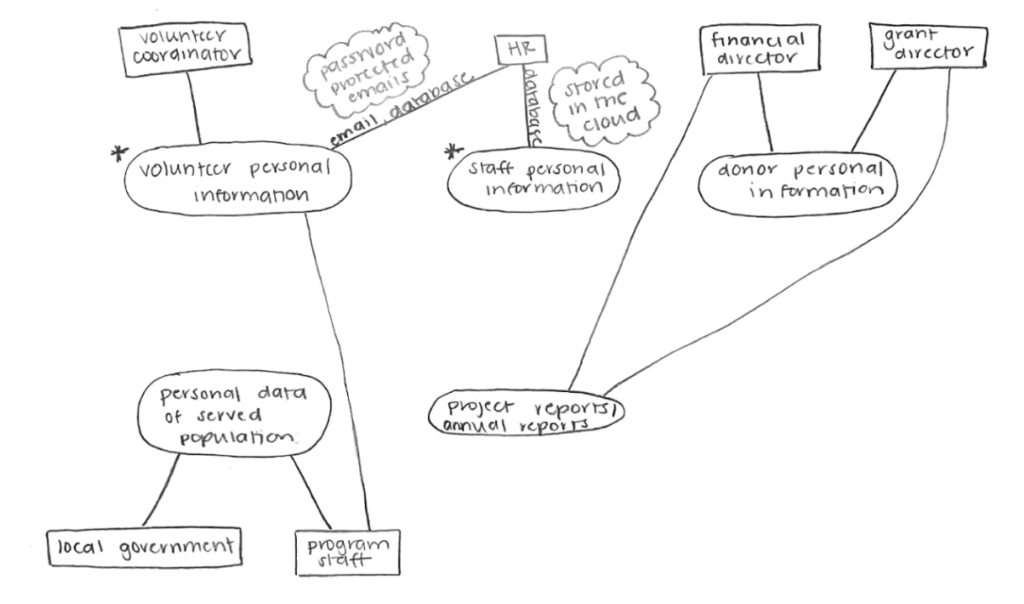
*This example was written from the POV of a Human Resources worker in a general nonprofit. Your models should be much more detailed and specific, this was just to give guidance.
Once complete, partner with another individual and talk through your maps. Share any points of surprise for you or anything this exercise brought to your attention. Feel free to share feedback with one another, this is meant to be a collaborative exercise.
Closing Discussion
As we have discussed over the last hour, data security is integral to the daily workings of a nonprofit organization and often arises in a variety of ways throughout the workday. Take a moment to share with a partner or the group how your perspective on data security has changed over this unit and what new practices you will employ in your work to ensure the safety of your data. Is there anything that surprised you?
Congratulations on completing this workshop! Please consider giving us feedback in our survey linked in the button below so that we can continue to improve our workshops.